10 major areas from QAX were listed for the 2025 Gartner® China Security Technology Hype Cycle Report
Date:Sep 15,2025 Author:QAX
"The focus of cybersecurity is shifting to ensuring AI security, driving business transformation, and enhancing organizational resilience," Gartner observes. "The market focus is shifting from basic compliance to more sophisticated proactive defence and data-centric security strategies."
Gartner® recently released the "Hype Cycle™ for Cybersecurity in China, 2025." According to the report: "CIOs and relevant leaders can use this Hype Cycle to identify practical, high-value technologies and practices to maintain organizational security and agility."
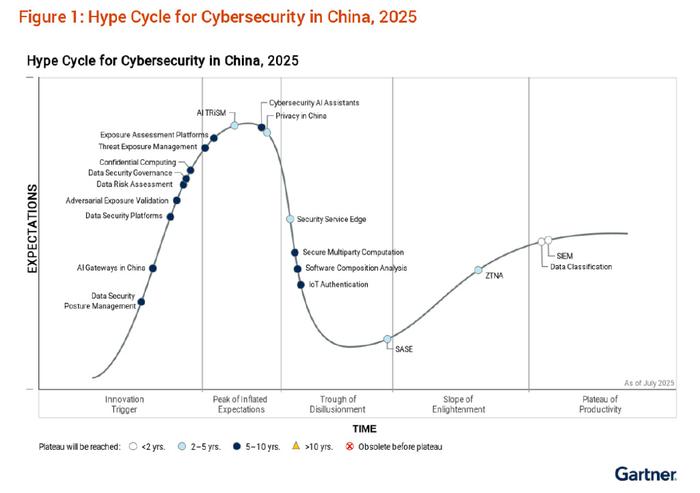
In this Hype Cycle, QAX is listed as a sample vendor in 10 key areas, including Data Security Posture Management (DSPM), China AI Gateway, Data Security Platform (DSP), Exposure Assessment Platforms (EAPs), Security Service Edge (SSE), Software Composition Analysis (SCA), Internet of Things (IoT) Authentication, Secure Access Service Edge (SASE), Zero Trust Network Access (ZTNA), and Security Information and Event Management (SIEM). We believe these areas cover the full range of security needs, from infrastructure protection to advanced threat detection and response.
Technology in its nascent stage: Data security is most popular security topic
Gartner observes that "data security remains the hottest security topic in consulting for Chinese organizations, driven by regulatory compliance requirements, data breach risks, and new security challenges posed by artificial intelligence." Data security platforms (DSPs), data security situation management, data risk assessments, and data security governance are increasingly becoming key areas of focus. "Security managers should carefully evaluate these emerging data security technologies to prepare for scalable and compliant data-driven growth."
The QAX Data Security Management and Control Platform integrates QAX's powerful data identification, threat detection, risk analysis, and response capabilities to help government and enterprise clients discover, classify, and grade data assets, monitor data flows, analyse security alerts, and implement coordinated responses. This platform provides comprehensive data security situational awareness and dynamic protection, fully meeting compliance management requirements and effectively mitigating data security risks. The product offers four key features: a clear overview of data distribution; comprehensive monitoring and discovery to visualize data flows; comprehensive security policies to detect data anomalies; and a variety of response methods to manage risk events.
As more and more enterprises adopt AI applications at scale, AI gateways have become a new innovative technology this year. Gartner notes, "AI gateways were introduced precisely to address this complexity. They provide a unified interface for managing API keys, setting rate limits, tracking usage and costs, and intelligently handling requests across different large language models (LLMs)."
In the AI gateway field, QAX has developed Large Model Guard (GPT-Guard), which focuses on addressing model security, data security, content compliance, and network security issues faced by enterprises using large models. By providing protection against hint word attacks, computing power consumption, and data leakage, it securely protects input and output content, safeguarding model operations from the OWASP LLM Top 10 attacks and preventing the leakage of sensitive data within the model, ensuring application security, data security, and compliance for enterprises using large models.
The period of inflated expectations: Shifting from passive discovery to proactive risk exposure management
"By 2027, 60% of large organizations in China will implement risk exposure management in their security operations centres (SOCs) to optimize incident response efficiency and reduce breaches." Security teams can more efficiently identify issues, prioritize them, and quickly remediate them.
In this area, QAX's products primarily include the Cyber Asset Attack Surface Management System (CAASM) and the automated penetration testing system (codenamed "Gatling"). CAASM's core capabilities include multi-source asset data fusion and analysis. By connecting to enterprise security systems, network devices, and IT infrastructure, it integrates and correlates data on assets, risks, policies, business, networks, organizations, and personnel. This allows it to continuously monitor asset security posture and accurately identify high-risk and non-compliant assets. Gatling simulates attackers and automates the complete attack surface collection and penetration testing process—from information collection and vulnerability detection to maintaining permissions and lateral movement. This helps clients effectively discover externally exposed attack surfaces, remediate security vulnerabilities, and strengthen their security defences.
Bubble Burst: Accelerated Development, Expected Economic Benefits Emerge
We believe that security technologies entering the bubble burst phase mean that enterprises and users are beginning to prioritize their practical impact and application value in real business scenarios, rather than their conceptual appeal. These technologies are gradually maturing and demonstrating their potential and commercial significance in practice. In this report, Gartner categorizes Security Service Edge (SSE), Software Composition Analysis (SCA), IoT Authentication, and Secure Access Service Edge (SASE) into this development phase.
QAX SSE utilizes a Secure Proxy Gateway (SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA) to effectively protect remote access to web, cloud services, and applications. The Secure Proxy Gateway (SWG) provides comprehensive website and application service traffic inspection and web security protection capabilities, as well as multi-layered network security protection features such as sensitive data identification, dynamic desensitization, and web and document watermarking, providing two-way web security assurance.
In terms of software composition analysis, QAX Open Source Guard uses an intelligent data collection engine to obtain open source software information and related vulnerability information globally. Leveraging its proprietary open source software analysis engine, it provides enterprises with open source software asset identification, open source software security risk analysis, open source software vulnerability alerts, and open source software security management. This helps users understand open source software asset information, obtain timely open source software vulnerability intelligence, mitigate security risks posed by open source software, and ensure the delivery of more secure software.
In terms of IoT authentication, QAX has launched the QAX IoT Security Access System (IoT-NAC) to help government and enterprise customers build a trusted IoT environment. Using mechanisms such as security compliance checks and network access authorization control, the system, based on active and passive analysis technologies, conducts security compliance checks for abnormal device status, unusual network behavior, and weak passwords. This helps users respond to and quickly address unauthorized devices within the network, enhancing the IoT and device's ability to resist intrusion and improving the overall security compliance of IoT devices.
Regarding SASE products, Qi'an Yunjing SASE is an intelligent system that deeply integrates network connectivity, data security, compliance management, and endpoint security, breaking the traditional stacking model of security tools. Leveraging a cloud-native architecture, it deeply integrates network and security capabilities to create a systematic "one endpoint, one platform, one cloud" solution, achieving "one agent for unified management, one platform for unified prevention," helping enterprises accelerate their embrace of the new era of hybrid cloud digital office.
Steady Recovery Phase: Zero Trust Matures and Becomes Widely Adopted
Zero Trust Network Access (ZTNA) is the only security technology to enter this phase this year. We believe this development demonstrates widespread enterprise recognition of the efficiency and reliability of Zero Trust in practical applications, with expanding application scenarios and a continued rebound in market confidence.
The QAX Zero Trust Network Access System (ZTNA) is cantered around data assets and adheres to QAX Zero Trust's four key capabilities: identity-based, secure business access, continuous trust assessment, and dynamic access control. Covering identity, devices, networks, applications, and data, it leverages dynamic access control mechanisms to continuously optimize access policies and effectively mitigate various access risks. Furthermore, the combination of QAX Zero Trust and Secure Space provides customers with a closed-loop access control system encompassing devices, networks, services, files, and data throughout the entire lifecycle, mitigating data leakage risks during business access and ensuring company data security.
Productivity Maturity: SIME is delivering stable, tangible benefits
In this stage, the technology has achieved a high level of maturity and stability after early exploration, improvement, and optimization. Security Information and Event Management (SIEM) at this stage has been widely accepted by the market and applied across multiple industries and fields.
Over the past year, QAX's Situational Awareness and Security Operations Platform, NGSOC, has deeply integrated advanced AI big model technology to create the QAX AISOC Intelligent Cybersecurity Operations Platform. Powered by a dual engine of security big models and a big data correlation engine, it embeds AI capabilities into the core and most expert-reliant security operations tasks—analysis, investigation, response, reporting, hunting, and policy creation. By streamlining repetitive and tedious manual operations and removing the vast amount of noise and complex information, it makes security operations truly simple, efficient, and worry-free, ushering security operations from manual to autonomous driving.
Gartner predicts that "by 2028, 60% of organizations deploying artificial intelligence technologies in China will adopt collaborative artificial intelligence defence strategies, integrating cross-functional teams to address the cybersecurity risks of artificial intelligence. This proportion will increase significantly from the current 5%."
Ref:
(CH)https://www.qianxin.com/news/detail?news_id=13685
(EG)https://www.gartner.com/en/articles/hype-cycle-for-emerging-technologies